UPDATE:I’m in the process of migrating my most popular articles and writing some new posts over at redflagsecurity.net. See the latest version of this post at this link.
Intro
Most IT people are somewhat familiar with Wireshark. It is a traffic analyzer, that helps you learn how networking works, diagnose problems and much more.
One of the problems with the way Wireshark works is that it can’t easily analyze encrypted traffic, like TLS. It used to be if you had the private key(s) you could feed them into Wireshark and it would decrypt the traffic on the fly, but it only worked when using RSA for the key exchange mechanism. As people have started to embrace forward secrecy this broke, as having the private key is no longer enough derive the actual session key used to decrypt the data. The other problem with this is that a private key should not or can not leave the client, server, or HSM it is in. This lead me to coming up with very contrived ways of man-in-the-middling myself to decrypt the traffic(e.g. sslstrip or mitmproxy).
Session Key Logging to the Rescue!
Well my friends I’m here to tell you that there is an easier way! It turns out that Firefox and Chrome both support logging the symmetric session key used to encrypt TLS traffic to a file. You can then point Wireshark at said file and presto! decrypted TLS traffic. Read on to learn how to set this up.
Setting up our Browsers
We need to set an environmental variable.
On Windows:
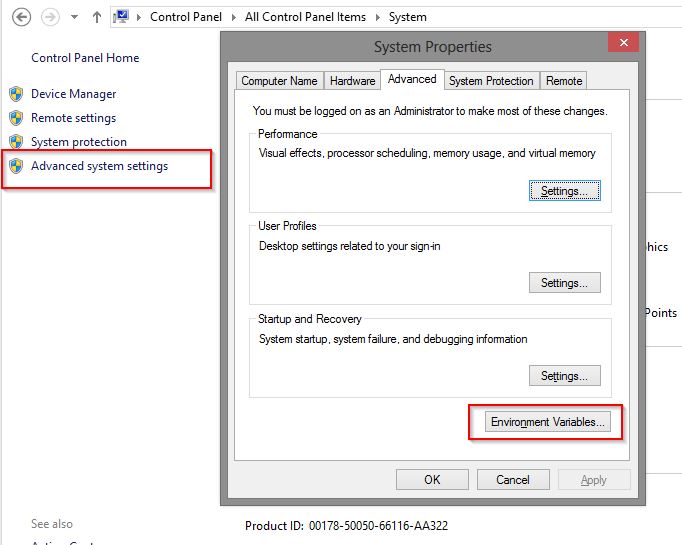
Go into your computer properties, then click “Advance system settings” then “Environment Variables…”
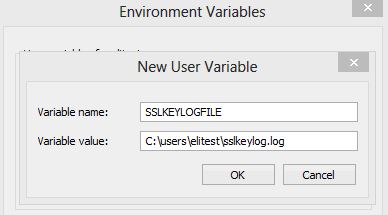
Add a new user variable called “SSLKEYLOGFILE” and point it at the location that you want the log file to be located at.
On Linux or Mac OS X:
$ export SSLKEYLOGFILE=~/path/to/sslkeylog.logYou can also add this to the last line of your
~/.bashrcon Linux, or
~/.MacOSX/environmenton OS X so that it is set every time you log in.
The next time that we launch Firefox or Chrome they will log your TLS keys to this file.
Edit: If you are having trouble getting it to work on OS X take a look at the comments below. It seems that Apple has changed how environmental variables work in recent versions of OS X. Try launching firefox and wireshark within the same terminal window with,
# export SSLKEYLOGFILE=/Users/username/sslkeylogs/output.log# open -a firefox# wiresharkThanks Tomi for sharing this.
Setting up Wireshark
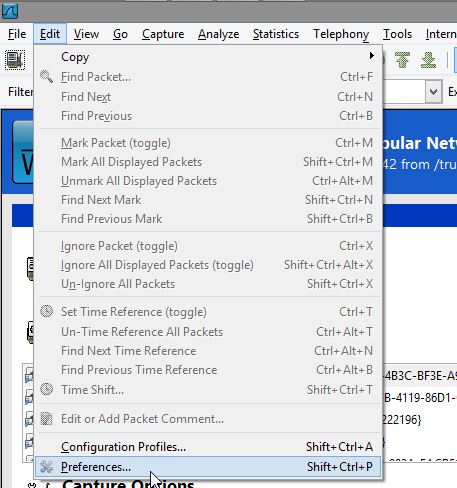
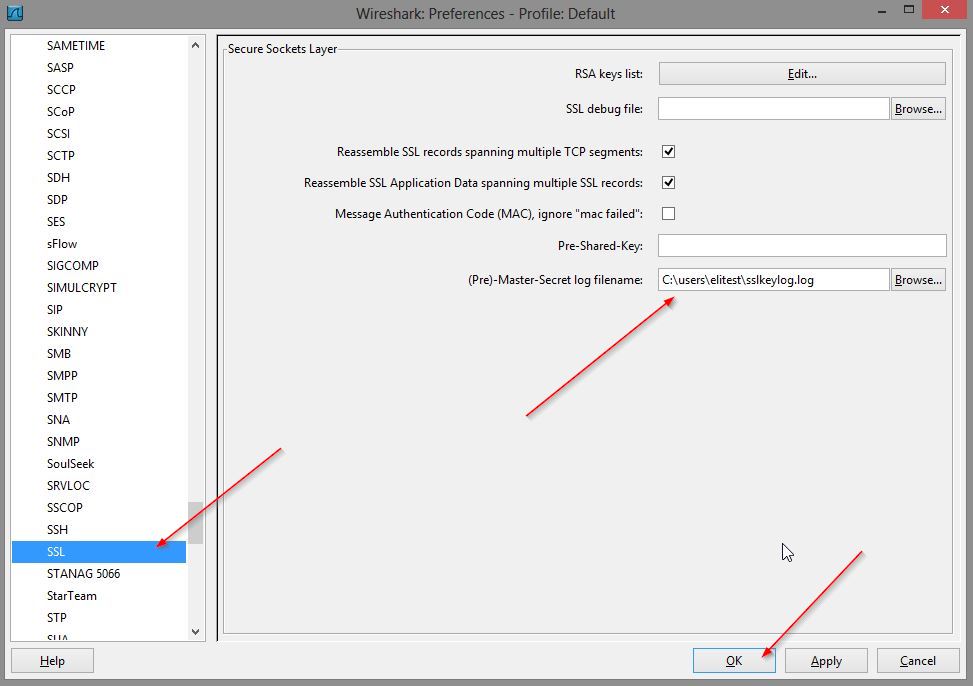
You need at least Wireshark 1.6 for this to work. We simply go into the preferences of Wireshark
Expand the protocols section:
Browse to the location of your log file
The Results
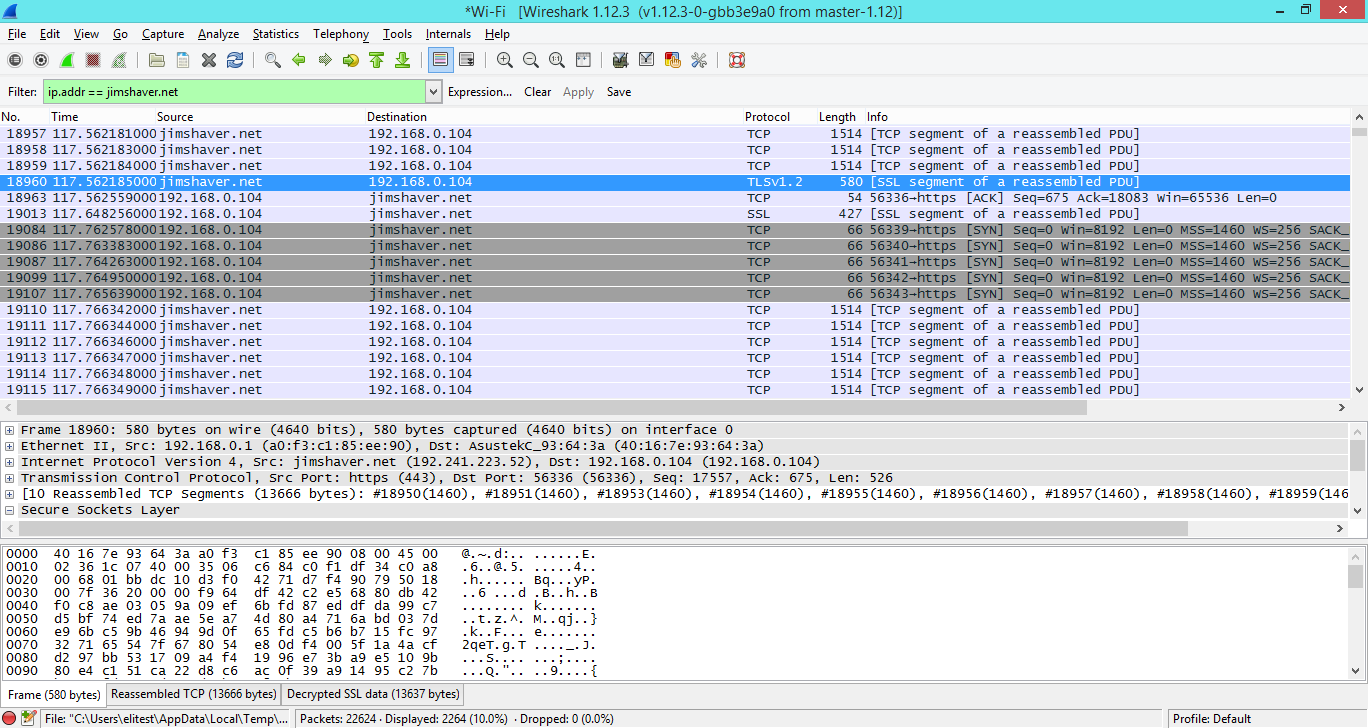
This is more along the lines of what we normally see when look at a TLS packet,
This is what it looks like when you switch to the “Decrypted SSL Data” tab. Note that we can now see the request information in plain-text! Success!
Conclusion
I hope you learned something today, this makes capturing TLS communication so much more straightforward. One of the nice things about this setup is that the client/server machine that generates the TLS traffic doesn’t have to have Wireshark on it, so you don’t have to gum up a clients machine with stuff they won’t need, you can either have them dump the log to a network share or copy it off the machine and reunite it with the machine doing the packet capture later. Thanks for stopping by!
References:
Photo Credit: Mike



![2015-02-11 22_30_28-_Wi-Fi [Wireshark 1.12.3 (v1.12.3-0-gbb3e9a0 from master-1.12)]](index_files/2015-02-11-22_30_28-_Wi-Fi-Wireshark-1.png)
Awesome article. Thanks for sharing this tip.
Awsome
I am using Wireshark 1.12, FIrefox 35.0.1 and Windows 7. I can see my SSL/TLS secrets being populated in my log file, but I am not getting the Decrypted SSL Data tab. Any thoughts on what I may be doing wrong?
And you have filled out the “(Pre)-Master-Secret log filename” field in your preferences? Be aware that Wireshark might be sniffing traffic that is not sent by the configured browser, e.g. a background application on the same system might be reaching out over TLS and wouldn’t be logging its keys. It will only show that tab for traffic it can decrypt. Filter out information so that you are only looking at the communication that you are relatively certain is coming from the browser.
I double checked that Wireshark is pointed at the log file. I shut down everything else and used the far side IP address to confirm which traffic I was viewing. I will need to keep digging.
The other thing to mention is that a lot of the data is still either gzipped or binary data like images, so it may appear obscured. But you should still get the tab, in any case.
He did say in the article that “You need at least Wireshark 1.6 for this to work.”. If you are using 1.12, it may not work.
Yeah but I think under their versioning scheme, 1.6 = 1.06 and therefor is older than 1.12.
When you look at the packets, you will need to check for a server key exchange packet….Apparently wireshark cannot decrypt ephemeral diffie-hellman encrypted data. So if you see a packet that says server key exchange, that’s probably what is happening….unless i’m wrong. Please let me know if i am.
Yeah that is incorrect. Wireshark can’t decrypt it if you give it the RSA private key of the server, but the keys that I log in the article are symmetric keys generated during key exchange. The whole point of doing this is so that you can decrypt traffic using both RSA, DH and DHE key exchange.
How are you sending the DH/DHE key to wire shark to decrypt the TLS traffic?
If you have configured everything right( i.e. keys are being logged to the file) and still seeing encrypted TLS traffic then it is traffic not coming from your browser.
Hi bro, I suggest you to try another way. Right click one TLS packet(Such as Client Hello), then click Follow SSL stream. Then you can see the decrypted plain-text data. Make sure that you imported the key log file correctly.
This guy had the same problem:
https://ask.wireshark.org/questions/30290/decrypting-tls_ecdhe_rsa_with_aes_128_cbc_sha-and-tls_ecdhe_rsa_with_aes_128_gcm_sha256-using-sslkeylogfile
Although he eventually figured it out, he used a slightly older version than yours. Maybe you need to tweak compile options and recompile.
It probably has something to do with forward secrecy. Perhaps it’s not supported in your version. If you visit a site that isn’t using FS:
https://tools.ietf.org/html/rfc5246
You should be able to decrypt this in Wireshark.
Actually it might be the mode of operation for the block cipher that’s the problem. Old versions don’t support GCM. But you are using 1.12…
Thank you for the pointers. I cycled through the security.tls.version.max options as you suggested and confirmed in the captures that the encryption protocol used was changing accordingly. Unfortunately, I am still not getting the Decrypted SSL Data tab, even when going to the IETF site you listed. I found some additional information here http://wiki.wireshark.org/SSL, a “wireshark -v” on my system lists GnuTLS 3.2.15 and Gcrypt 1.6.2. I am using the latest stable version that comes in the Windows installer so I have whatever compile options that it is built with. I will keep digging.
Hi, just wondering if you found the ansewer yet 🙂 I share the same problem! Thank you
I’ve just found this discussion because I had a similar problem. I captured a nonstandard SSL port and Wireshark didn’t recognize the protocol as SSL. When I added my port number into Preferences/Protocols/HTTP/SSL/TLS Ports, it worked immediately.
Thanks a WHOLE LOT! Had the same problem with non-standard SSL port and your comment is the one that helped me to get the result.
Not sure why the log file doesn’t get populated on my Mac … set the variable:
$ set | grep SSLKEY
SSLKEYLOGFILE=/Users/papaia/SSLkeylogs/sslkeylog.log
and running FF 35.0.1 ???
Yeah I didn’t actually get to test this on a Mac as I no longer own one. Looks like OS X did some redecorating recently with environmental variables see this. Maybe it needs to be a system environmental variable on OS X?
Use “launchctl setenv SSLKEYLOGFILE=~/Users/papaia/SSLkeylogs/sslkeylog.log” instead of export.
launchctl setenv SSLKEYLOGFILE /Users/papaia/Desktop/sslkeylog.log
You can use EXPORT command to populate MacOSX environment variables — you just have to sudo now.
Setting an environment variable with EXPORT will only apply to that session. Launching a browser or other web client outside of the session will not have the environment variable set.
If using EXPORT to set SSLKEYLOGFILE, you’ll have to launch Firefox from the same session.
Any remotely recent version of Chrome will work just fine now. At the time of the cited blog post (look at the timestamp), the feature was new in NSS had only hit dev channel.
Or use Cloudshark, just drag the key onto the web page and then hit decrypt. Its nice because I can let my IT minions debug pcaps without me giving them the TLS keys to the kingdom!!! Course, Cloudshark isnt free like wireshark even though its based on it
Thanks for the blog entry, much appreciated.
My question is, what benefit would one get by using Wireshark to MitM encrypted web traffic as opposed to BurpSuite? (http://portswigger.net/burp/)
If there is no benefit, then probably BurpSuite is the easiest way.
With Wireshark your not doing an active MiTM nor swapping certificates. If you’re troubleshooting an application that does certificate pinning you might prefer to use Wireshark 🙂
s/your/you’re. Sorry, it hurts my eyes as well 🙁
Great stuff!
And you got the SSL line or it’s just the tab you can’t see? I didn’t see mine coz I was with a proxy. It seems it encapsulate https in http, so you can’t use it to spy on your mates (in this case, at least). Neither you can use it to see app/malware that use their own conection.
I’d like to be give a practical exemple of how to use it.
Nice post, btw. 🙂
Can you think of a way to do the same with a mobile browser? Can’t quite find the same set of options for the mobile browsers.
I tried this on Linux Mint 17.1 and FF 35.0.1, double checked that the environmental variable has been set correctly, rebooted and reloaded this page, but no sslkeylog.log was created. Is a specific Linux distribution needed to make this work?
Is the path that you are pointing at an absolute path that you would have write access to? For example /home/username/sslkeylog.log?
export says
declare -x SSLKEYLOGFILE=”/home/jrv/sslkeylog.log”
where jrv is my username and I have write access. More help would be appreciated.
Hmmm…. I don’t have a (graphical) linux box close at hand. I’ll test in a vm this weekend.
I ended up making the file beforehand and then running the export command and starting firefox. Then I had content in my file (mint 17/ff 35)
Hi Jim,
This is a grate tutorial. I have just followed it and it works a treat.
Can I ask a question though.
Is there a way to copy/paste the ASCII from the “Decrypted SSL Data” tab?? The text is in a small column and would like to be able to copy it into notepad.
Is this possible or am I missing something?
Thanks
Great stuff, thanks Jim!
I got my OS X working only when firing up all related processes using exactly same Terminal-window like this:
1. Open ‘terminal’
2. # export SSLKEYLOGFILE=/Users/username/sslkeylogs/output.log
3. # open -a firefox
4. # wireshark
This worked for me.
The SSLKEYLOGFILE was not being written after following the above procedure. (Mac OS X Yosemite). I spent a few hours trying to figure this out. The environment variable is being set right. Finally I realized that killing Firefox by clicking on the x (top left) did not actually kill firefox process, I had to use force quit to kill Firefox. Once I did this and followed your procedure it worked fine. Thanks to Jim Shaver and Tomi.
Thought this might save a few minutes for another developer.
I tried everything that you said. But, I am unable to decrypt SSL/TLS data. I set an environment variable to the specified path and tried restarting firefox. but, the decypted text tab is not visible in wireshark. Can you please help me out?
Hey Tomi !! I tried doing the same thing in my MAC OS. But, I am not getting the Decrypted Tag. Can you please help me out with this?
Thanks Jim!!
The sslkeylog file doesn’t get populated for me. Is there another setting I need to do.
I was hoping this was another Lenovo story…
But this is more useful and less funny.
I’ve been searching the entire internet for this answer! thank you dearly
How do I get the TLS key for other applications connections? I want to monitor a jar application right now, and it uses TLS.
http://jsslkeylog.sourceforge.net/
Amazing, thanks
Amazing! (FF wants to be secure??)
Thanks for that info!
Does Wireshark continually read the file, seems FF adds more keys while opening new https-Pages.
I also miss the ssl-decode Tab (FF Ver 1.8.2, newest for Debian stable). But I have a Analyze->Follow SSL-Stream menu. Is that the same? In most cases this opens an empty window (I think contents cant be decoded). Whats the purpose of Analyze->DecodeAs (SSL) ??
Not all data can be decrypted using this method, often times Wireshark sees more SSL/TLS data than what is just from Firefox. It continues to read the file as I recall.
I could really use some help here. I have some Wireshark packet captures saved on an external HD, I needed to decrypt the SSL. Where would I find the key to do this? UGH!!!!
Yeah I bet. You and the NSA and every identity thief. Unfortunately if the keys are not dumped at the time that the traffic is sent there isn’t a way to decrypt it, that is the point of SSL/TLS. As mentioned early in the article, if you have the server’s private key you can also feed that into wireshark, and it may be able to decrypt the traffic, but this depends on many things, including the security of the key exchange method negotiated between the browser and the server(RSA vs DH(E)) as well as availability of the private key to you.
How web browser and server know exactly what is the key used for their private communication? Don’t they have to at least send this information over once?
That is what public key cryptography(TLS in this case) does. See this diagram for a decent explanation of how that works.
What can you do to decrypt traffic from a Widows server making a HTTPS calls to another Windows server if it does not use Firefox or Chrome. For instance I have a front end CRM server making a call out to a BizTalk server for a specific URL using 443. I have the proper key from the BizTalk server imported into my Wireshark but our users use IE not Chrome or Firefox and the CRM server making the call does not either so a sslkey file does not help in my case or at least it seems from the post only Chrome or Firefox create the log file. We see intermittent issues are happening between CRM and BizTalk over 443 and we are trying to find out what is the cause, but our packet captures will not decrypt because of TLSv1 and TLSv1.2 does not have the master key or some other constraint for decrypting. Surely someone has figured out how to decrypt SSL traffic from IE or Windows.
If you wanted to use wireshark you could try loading the private key of the server into wireshark if you have access to it. But that will only work if your BizTalk server is using RSA ciphers. If it really is HTTPS and not just ‘something else’ over TLS then you may want to look into SSLSpoof or SSLSplit which will allow you to Man in the middle the SSL connection, and if you do it correctly, pipe it into wireshark(I would consider this the ‘Hard way’). Or use a tool like mitmproxy(for which I am a contributor) or Fiddler(more windows friendly) to analyze the traffic. These tools are http(s) specific analysis tools rather than a general network analysis tool. The only thing you really have to figure out with these is how to pipe your CRM’s traffic through the proxy and get the CRM system to trust the proxy’s certificate.
Hi, all this is great information!
In my log file I see only ‘Client_Random’ not RSA output. Does that mean RSA is not used as method? I think this I why I don’t see any decrypted data tab. Appreciating your help:)
Try to resize your editor window so you see the hole key on one line. I thought this too, and then recognized that there are only a few rsa keys if any. if you don’t have any at all, try to capture a login on youtube or googledrive or something. then you should have some rsa values.
Beware: if the selected cypher suite uses ephemeral modes of DH you will not have the needed keys in your log and will not be able to decrypt your traffic. At least that#s what I have found out so far playing with this stuff and searching the web 😉
Hope this helps. Let me know if you find better info than me 😉
Does this still work? My variable does not get populated. Using Kubuntu 15.04 and Firefox 41.0.1 or Chromium 45.0.2454.101
Yes, it does 🙂 I have to start the browser from the terminal, otherwise the keylog file stays empty. Now I have the problem, that I cannot see the HTML body. The HTML header gets encrypted, but the rest of the package is still jiberish. Thanks for this nice tut. helped me out a lot already 🙂
I am having the same problem. Can’t see the HTML body. Do you know if there is any way out?
Thanks a lot for this very good article.
One question, how did you find this SSLKEYLOGFILE variable? In FF sources?
I think I had either seen it in the Wireshark docs, or on someone else’s blog. But the format that it was in was so technical and opaque that I thought I could do it better.
Thanks!
Hi, I am struct at providing the pre-master-secret to Wireshark to decrypt the RSA Premaster key. I have the 48 bytes of pre-master-secret, but i don’t know in which format i have to give. Could some one please help me. Thanks!
Cant get this to work now (it used to work before) Has anything changed with OSX 10.11.3, Firefox 44 or Chrome 48?
I’m sorry but I do not run OS X. I have heard that Apple has done some changes over the versions to how environmental variables. Take a look through the rest of the comments, if that doesn’t work you may have to do more research elsewhere.
I had a the problem last week that ff would not write the keys into the sysvar. that happened after an update. After having that problem on kubuntu and debian i figured it must have been an update of the kernel or something like that. One week later… so today, i made another sys-update and it works again 🙂 so maybe you’ll just have to wait a few days until apple finds out that they killed the feature 😉 good luck!
No luck with this method. I can get it to work as describe but it basically does the same as the “Live HTTP Headers” plugin for Firefox. You get to see the headers.
The headers are encrypted too, are you seeing session keys written to the file? A lot of the data may look like garbage, but that is because most website data are binary images.
I guess this is what you are supposed to get. But you go not get the decrypt tab
Great explanation, thanks so far.
But reading out until here, using all hints above, I was unable to get Firefox populating this sslkeylog file. I am using Win7 (64 Bit) and the current Firefox version 45.0.2
The only hit I found was on https://developer.mozilla.org/en-US/docs/Mozilla/Projects/NSS/Key_Log_Format
saying that this feature is disabled in Firefox 48, which confused me totally, since we are currently on 45. Or do they have a time machine?
Thanks for bringing this to my attention. I found the relevant bug associated with this and have added my comments. Anyone with strong feelings on the matter should do the same.
https://bugzilla.mozilla.org/show_bug.cgi?id=1188657
Thanks for taking care of this. By the way, in the meantime I installed Chrome in parallell to Firefox and was also unable to populate the sslfkeylogile with it. Do you know whether the Chrome people removed this feature as well (although stated otherwise in the discussion you pointed me to)?
Not sure. I believe chrome was going to switch from NSS to OpenSSL(BoringSSL). If they have done that it would break this functionality.
I am using rsa 2048 bits long key and certificate in apache webserver. i am using key log file and debug file in SSL preferences and setup the path to my generated private key.
Hello Jim,
I have my localhost running on Apache 2.4.20 on port 443 for http-2 and I need to capture this traffic. I have created a self-signed certificate and key for apache webserver configuration.
Kindly suggest on how to proceed further in this case.
Regards,
Ankush.
Thanks, really helped me a lot 🙂
You are the fountain in my desert my friend! This is an awesome article. Thank you!
Glad it helped.
I tried the SSL decryption on the https accesses from my own laptop and it works perfectly!
I have SPAN configured on my Cisco switch that forwards all traffic to my Laptop’s interface.
So i followed what you said at the conclusion, the “or copy it off the machine and reunite it with the machine doing the packet capture later”. But the Wireshark captures still says TLS — Application data.
What could be wrong?
So you are capturing session keys on the clients whose traffic is being sent through the span port?
Thats right. I’ve configured the client PCs to log their ssl keys and save them locally. Meanwhile, I capture traffic through the switch on my admin Laptop. I later get the logs from the client PCs to use with my wireshark.
This doesn’t seem to work like when I decrypted traffic from the laptop i’m at.
Thats right..
Excellent article!!!. Really appreciate it.
This is great for Wireshark users. I hope that Telerik will add it to Fiddler, if it’s at all possible (https://fiddler.ideas.aha.io/ideas/FID-I-65)
Well, it seems this method does’t work with Firefox 48+ anymore (see https://developer.mozilla.org/en-US/docs/Mozilla/Projects/NSS/Key_Log_Format).
Maybe, perhaps, in Firefox 50 will work again, but, meanwhile…
Hi. Nice article. I notice that this is good to decrypt secured connections on the fly. How can an encrypted captured packet be decrypted with/without the key provided. Thanks.
Hi, this works without importing the server key file to wirershark, right? Thank you!
Correct.
Hi, thanks for the great post.
I can see the decrypted data now.
However, it seems still unreadable, do you have any advice on help understanding the real content?
Thanks.
how to do it without manually not cofiguring ?
How do you do it with a mobile phone? iOS preferably
I would look at mitmproxy. It allows specifying SSLKEYLOGFILE as well. If you are capturing the traffic with Wireshark at the same time you could see it decrypted. With the added benefit of handling https really well too.
Thanks a lot!
Here’s a quick recipe for fellow Ubuntu users:
“`
# install latest WireShark
sudo add-apt-repository ppa:wireshark-dev/stable
sudo apt-get update
sudo apt-get install wireshark
# install latest Firefox just in case, see https://bugzilla.mozilla.org/show_bug.cgi?id=1188657 why
sudo apt-get install firefox
export SSLKEYLOGFILE=/home/user/sslkeylog.txt
firefox google.com?q=hello
ls -l $SSLKEYLOGFILE
“`
After that continue as instructed.
Hey man,it’s really help.However,I only can see the header of the html,and can’t see the body.Is there anything wrong?I’m sure I did right.
I’m on a Mac, and I got the sslkeylog file created when I launch Chrome, and set up Wireshark fine, but inside of Wireshark I don’t get the Decrypted SSL Data tab like you mention. Is that something else I should have to set up, or should it just show up?
Keep in mind Wireshark is capturing traffic from more than just the browser. The tab will only show on traffic that it can decrypt. If there is TLS traffic from the underlying operating system or other program then that will not be decrypted.
That’s unfortunate. I’d like to investigate some suspicious traffic generated by a proprietary software I’ve been using for work, but it’s not browser based. Can you think of an alternative way to get at it?
Just a heads up, since Oct 2015 Chrome has changed to make use of command line switch
--ssl-key-log-file="[file]", and probably doesn’t respect the environment variable anymore (at least I can’t get it to work now). Here is the reference:Missing your reference, but yes on MacOS the latest Chrome doesn’t log, but Firefox still does.
$ export SSLKEYLOGFILE=~/sslkeylogs.pms
$ open -a ‘Google Chrome’
# Do some browsing…
$ cat ~/sslkeylogs.pms
cat: sslkeylogs.pms: No such file or directory
$ open -a ‘Firefox’
# Do some more browsing…
$ grep -v “RANDOM” ~/sslkeylogs.pms
# SSL/TLS secrets log file, generated by NSS
RSA 49fc07ee96dd6834 030380e9f142b7a60c4d8e055fbdd0a2a63fc11e90d0cca999d2e5464c84bbe93f828b60882c3ff057d2ac89daa25bbc
OK found your reference, this works on Chrome 56 on MacOS 10.12.3 (Sierra)
$ open /Applications/Google\ Chrome.app/ –args -sslkey-log-file=~/sslkeylogs.pms
$ echo “” > ~/sslkeylogs.pms
# cleared the log file, then do some browsing
$ grep -v “RANDOM” ~/sslkeylogs.pms
RSA 510b7ba134c2f215 0303c83bea22ebf1548c80951f8e3ebc3662752412c4ee2b81f4ff7d49fc41343dedd0cb59b32cd1da630e5170d2fc03
RSA ab47b6aaefb00008 0303f74edcf0ef331de7f2ea32817f3dc2c801c08f93f2116e7c2e08af68a60123ed704ce2032f09e1342b378f2ef57f
Does this still work for you? I am not able to get it working with Chrome 58 / Sierra (10.12.5)
Chrome has been talking about enabling this only in developer builds. Otherwise I’m not sure why it isn’t working for you.
I am unable to locate my SSLkey log file. Can you please help me where to locate it?
Dude!! I am unable to locate the log file. Can you please help me out with it?
Thanks, nice post
hi, i want to know the version of wireshark , i am using the wireshark v2.0 , and another problem is how to open the `decrypted SSL data` tab , i can not find it,can you help me?
Does this tutorial work in Kali Linux ? I set correctly the environment but the file sslkeylog.log doesn’t create. Any ideas? Note: I check the same tutorial in Windows 10 and it is worked.
is there anyway to export keys without using browser. i am using java webdav session from client to server. how should i export keys
As mentioned at the bottom of the article take a look at http://jsslkeylog.sourceforge.net/.
it seems that it does not work. would you please provide exact information so that to use that.
Hi, Jim – I’m using wireshark 2.2.6. I don’t seem to have the ‘Decrypted SSL Data’ tab at the bottom of the Packet Bytes window as illustrated in the screen shot above. Nor can I seem to locate an option to make it visible. Do you know where I may be missing the boat on this? Thanks in advance.
Are you sure the traffic you are looking at is associated with the browser traffic? Or is it other encrypted traffic that your computer was generating?
how would i decrypt the SSL from a .pcp file? is it the same process?
I’m troubleshooting issue related to Internet Explorer, I identified that IE doesn’t dump the session keys. is there any way for IE to dump the session keys?
Thanks a lot Jim! I can now see the log created by launching Chrome through windows terminal. However, there is nothing written so far while the Wireshark shows there are TLS traffic….
Can we use SSLKEYLOG file technique with TSHARK ?!
hello Jim
i have few question arises in my mind… i have pre-master secret using jssl-key log. now how or what process can i decrypt without using wireshark and would like to see on tcpdump in CLI?
is it possible to make own decryption system using openSSL and providing pre-master secret.
i am searching of this solutions
Thanks for the great tutorial!
I’ve struggled with Chrome v.61 on Mac OS Sierra, and no matter what I’ve tried it did not capture anything, but finally after installing Chrome Canary v63 it did worked again just with “export” and starting Canary from the same terminal with open -a app. Looks like variable is disabled in regular Chrome version. In Firefox still works fine starting from the same terminal.
$ export SSLKEYLOGFILE=Documents/sslkeys.log
$ open -a Google\ Chrome\ Canary
Cheers,
Awesome article
How to save the SSL decrypt in .pcap format
How call Wireshark for logging programatically in Windows for TLS troubleshooting in Client ?
” getting a network capture on a Windows computer even without NetMon is easy and scriptable. NetSh.exe, the “Swiss Army knife” of Windows networking, can be used to collect a network trace.”
https://blogs.technet.microsoft.com/tspring/2015/02/23/poor-mans-guide-to-troubleshooting-tls-failures/
Thanks very good article
For those on Mac OSX with Chrome v67 and are struggling to get it to work, I was able to get production Chrome (not Canary) to work by invoking it via the command line as follows:
open -a /Applications/Google\ Chrome.app/ –args -ssl-key-log-file=’/Users//Documents/sslkeylog.txt’
Note the fully qualified filepath, quotes, and be careful with the dashes (I think wordpress formatter converts them to en/em dashes; for reference, use double hyphen for ‘arg’ and single hyphens for ‘-ssl-key-log-file’).
I tried on Windows and MacOS but no “Decrypted SSL data” tab
Hi Jim,
Nice article, it works wile I am testing with browser on the same laptop that has wireshark installed in. I really need your help why this setup not working while I am trying to decrypt packets sent from other ports( test device e.g. apple tv) to my laptops port which has wireshark installed.
So my set up is like this;
I have apple tv connected to a cisco switch with port mirroring capability. then I have my test laptop connected to the same switch with wireshak installed. then I set up port mirroring in the switch to send network sniff all network calls of apple tv to my laptop’s port. then I start wireshark to watch all calls. I can see all network calls, but the ones are encrypted not decrypting.
I would really appreciate your help. I know I must be doing something wrong?
cheers;
som
Howdy Jim, thanks for sharing. This is a real nice “trick”. I can see the HTTP2 traffic that was previously encrypted.
As a point of reference, I made this work on:
Windows 7 Enterprise SP1 (Running on Virtual Machine)
Firefox: 63.0.3 (32-bit)
Chrome: Version 70.0.3538.110 (Official Build) (64-bit)
Do you know of a way to make this work with MS Internet Explorer? I quickly tried on my VM, but I guess IE isn’t using those NSS libraries from Mozilla so Wireshark couldn’t decode IE’s traffic.
Thanks,
KH
Nope. Ask MS.
Hi, thanks for your excellent description. It works fine for me! I’ve one question related to the decryption which is done by wireshark. Is it possible to do it manually with openSSL in a commandline interface. Which part of the log-file is taken by wireshark and how are the packets decrypted? Thanks in advance, Markus
Hi , After decrypted packets we are getting https secure data how to get http dataThanks in advance.
HI Please can you help me because i am so confused where and what file i have to put in wireshark
I just stumbled on this and I do realize this is an old post, however I’m going to give it a shot. Using the keyfile environment variable I am able to get a key file to generate using Chrome. However, I haven’t been successful in getting a keyfile to generate using IE. The version I am using is 11.959.18362.0. Any ideas on how to get this to work?
log file is not generating on my side i am using ubuntu linux